We know Facebook has big plans for the Metaverse. The company even rebranded as Meta to underline it’s ambition. On Labstalk, we almost spent the entire season discussing benefits and goals of the technology, alongside with all the other tech topics in the same space, like Web3, NFTs and DOAs.
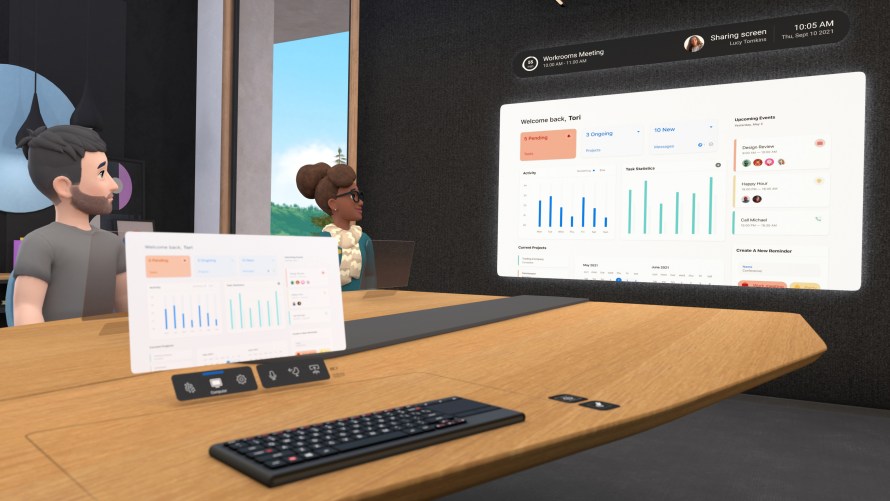
Back to Meta (the company) and the Metaverse: among others, one of the foundational use-cases the company re-imagines – to make it attractive to the promising B2B market: virtual or remote meetings.
And if you ever get to see any of the promotional images: At first glance, these that really look like a meeting in a 3D Room can be a viable alternative. In the pandemic the corporate workforce first came from plenty of travel and got force-used to Zoom and Teams meetings, only to develop even worse meeting fatigue because in-person required travel. Now after almost three years of pandemic, the audience is eager for something new and the time seems right for a different format.
Alone: the hype doesn’t materialise.
Parmy Olson from Bloomberg reports that Accenture, among other companies that are reference customers to Facebook/Meta’s Occulus platform, bought plenty of gear, 60k devices, some as long as 2 years ago. To use these devices for new hire orientation. AstraZeneca, another major customer, wouldn’t even comment.

The virtual conference room needs to die. VR is better used for fun and building relationships.
Source: Meta’s VR Headset Quest Won’t Replace Zoom – Bloomberg
A major reason for the lack of momentum I can confirm from own experiences is the bad reputation Facebook/Meta has for their perspectives on privacy and handling of sensitive data. The ‘surveillance capitalism’ approach the company takes with this new technology and economy bet becomes apparent in the pricing strategy for these Occulus devices. The Facebook/Meta (or ‘surveillance’)-free version of the device, that appears technically identical, is about 30% more expensive, according to sources in well informed circles.
Personally, I believe in the concept but can re-affirm these concerns and understand the restraints that come alongside the curiosity. While the investments that Meta makes in the technology help the hardware make necessary progress towards user-acceptance, other players need to step in and provide applications to help solve corporate acceptance.