You’ll be safe, they said. Until Microsoft told more customers, their email have been stolen.
Tag: leak
-
Grafana Incident
Grafana leaked their package signing key. Along with the passphrase. I felt like you should know.
-
Datenreichtum
Datenreichtum bei Flexbooker, 3.7 Millionen Benutzer betroffen.
-
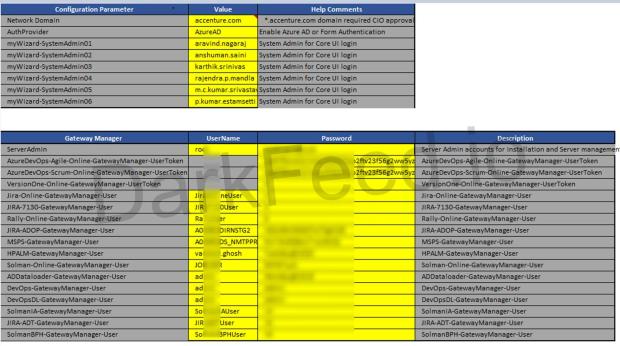
LockBit Group published Proof for Accenture Hack
darkfeed.io has published material the LockBit Group provided to proof their hack of the Accenture Network.
At first glance, it looks huge and worrying. Social media response at this time appears to acknowledge the proof.More here: LockBit 2.0 Proof for Accenture Hack – DeepWeb intelligence Feed
-
Clubhouse leakt 3,8 Milliarden Telefonnummern
Clubhouse. Das war diese App, die vor einem halben oder ganzen Jahr so unglaublich gehyped worden ist. Man kam nicht rein, das war Invite Only. Man kam nicht von alleine rein, cool waren nur die, die drin waren. Alle in meiner Bubble hatten FOMO, Fear Of Missing Out.
Diesen menschlichen Effekt haben vor 15 Jahren schon Facebook und Google mit seinem Mail Produkt sehr erfolgreich bedient. Das Ergebnis war, dass JEDER unbedingt eine Einladung wollte. Und mit Erhalt der gleichen wirklich äußerst bereitwillig Ihre Adressbücher freigegeben haben.
Für die Experience.
Zwischenzeitlich kann man verbale Ansprachen auch auf Twitter halten und kein Hahn kräht mehr nach Clubhouse.
Trotzdem sind der App jetzt 3,8 Milliarden Telefonnummern weggekommen. Und so wies aussieht seid Ihr auch dabei, wenn Ihr jemanden kennt, der das damals toll fand.
via futurezone.at
-
500M LinkedIn Profiles
Just after Facebook lost 500M user profiles to the public Internet, it’s LinkedIn’s turn a week later. Wherever data is collected, data is subject to breach or theft.
Like the Facebook incident earlier this week, the information — including user profile IDs, email addresses and other PII — was scraped from the social-media platform.
From the articlevia threatpost.com
-
Facebook Data Leak
Just in time for Xmas, Facebook dropped a huge package of user data.

Mark Zuckerberg More than 260 million U.S. Facebook users’ IDs, phone numbers, and names were exposed to an online database that could potentially be used for spam and phishing campaigns. Comparitech reports that before the database was taken down, it was found on a hacker forum as a downloadable file.
Source: Facebook Faces Another Huge Data Leak Affecting 267 Million Users | Digital Trends
-
Facebook lost phone numbers
Again, it’s Facebook, that made news with a data breach. TechCrunch reported first about midnight Euroean time, but it’s all over the news by today, noon. It’s time to realize social media is a mistake.
-
What We Can Learn from the Capital One Hack
Capital One Earlier this week, it became public that Capital One was victim to a privacy leak, affecting more than 100 million of their customers. News revealed details about the source of the attack, that apparently an individual conducted and bragged about it publicly.
Now, a few days later and more facts known, the always excellent Krebs on Security blog offers some lessons learned from the incident. It has good statements from Netflix, CloudFlare, DisruptOS and AWS personnel, including citations about the involvement of IAM, EC2 and WAF. In particular, it points out mitigations that AWS recommends in response to Server Side Request Forgery (SSRF).
Interesting is the conclusion that Rich Mogull comes to, that the industry is facing a major gap in skills, related to this kind of cloud security. Basic skill and availability thereof has always been a major gap in the entire industry. Only with the arrival of cloud it becomes more sparse. Mostly, because corporations maintain both their existing data centers and new cloud infrastructure, leaving out on the opportunity to become more secure in the cloud.
-
Google stored G Suite passwords in plaintext
In today’s edition of privacy related topics, it is Google that apparently stored customer passwords in plaintext. Google didn’t disclose which (enterprise) customers have been affected, but was clear that improper access is out of question. With this recent incident, Google joins ranks of Facebook, Instagram, but also Twitter and LinkedIn.
Google says it discovered a bug that caused some of its enterprise G Suite customers to have their passwords stored in an unhashed form for about 14 years.
Source: Google stored some G Suite passwords in plaintext for 14 years