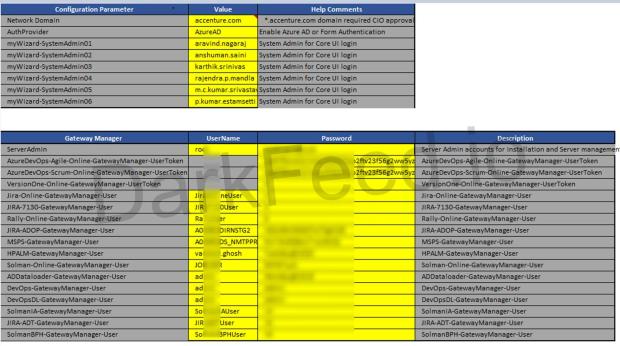
Google is paving the way for Gemini to completely replace Google Assistant on Android devices with a significant upcoming update. Starting July 7th, Gemini will gain the ability to control various phone features and apps, such as making calls, sending messages via Phone or WhatsApp, and utilizing utilities, even if a user’s “Gemini Apps Activity” setting is disabled. This is a crucial change, as previously, turning off this activity setting prevented Gemini from performing these convenient, integrated tasks, forcing a trade-off between privacy and functionality.
The update addresses initial confusion and privacy concerns by allowing users to leverage Gemini’s personal assistant capabilities without contributing their conversations to Google’s AI training datasets or product personalization efforts. Google has clarified that this is “good for users,” providing more control while ensuring that Gemini interactions won’t appear in the activity log when the setting is off. Although conversations will still be temporarily saved for up to 72 hours for security, this move effectively decouples functional device control from AI data collection, making Gemini a more private and powerful assistant ahead of its full Android integration later this year.
—
👉 [Read the full article]